YubiKey’s are low cost authentication tokens which can operate as personal identity verification (PIV) smartcards for Windows authentication.
This post provides a quick guide to configuring a Windows 2012 domain to authenticate using a Yubikey instead of a standard password.
Driver Installation
Download and install the YubiKey driver on all systems which will be using 2FA:
https://www.yubico.com/products/services-software/download/smart-card-drivers-tools/
Unpack the cab file using the expand command:
1 2 3 4 5 6 7 8 | expand YubiKey-Minidriver-4.0.0.162.cab -F:* C:\ykmdMicrosoft (R) File Expansion UtilityCopyright (c) Microsoft Corporation. All rights reserved.Adding C:\ykmd\README.txt to Extraction QueueAdding C:\ykmd\ykmd.cat to Extraction QueueAdding C:\ykmd\ykmd.dll to Extraction QueueAdding C:\ykmd\ykmd.inf to Extraction QueueAdding C:\ykmd\ykmd64.dll to Extraction Queue |
(Right click on the C:\ykmd\ykmd.inf and select install)
Create a Smart Card Certification Template
Open certtmpl.msc on the server.
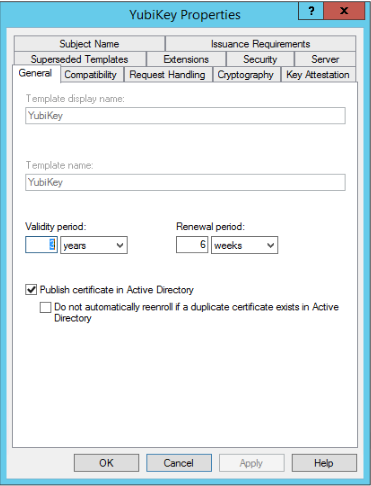
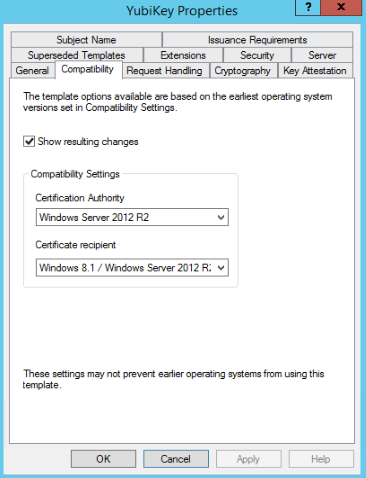
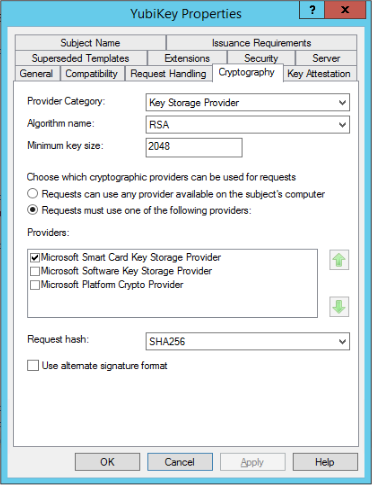
Find the SmartCard Login template, and select duplicate. Set the new name to “YubiKey”.
On the “Security” tab make sure users who will be using smart card authentication have permissions:

Change the options as below:

Add the created Certification Template to the CA
- Open certsrv.msc
- Select Certification Templates
- Right click in a blank area on the right side and select “New” > “Certificate Template to issue”
- Select the “YubiKey” template and click OK.
Active Directory Auto Enrollment Configuration
Create a new GPO called YubiKey and configure the following options:

Ensure the GPO is applied to users who will be using smart card authentication.
Client Configuration
Force the client to apply the group policy changes:
1 | gpupdate /force |
Verify the registry changes have been made:
1 2 3 4 5 | reg query "HKLM\Software\Policies\Microsoft\Cryptography\AutoEnrollment"HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Cryptography\AutoEnrollmentAEPolicy REG_DWORD 0x7OfflineExpirationPercent REG_DWORD 0xaOfflineExpirationStoreNames REG_SZ MY |
1 2 3 4 5 | reg query "HKCU\Software\Policies\Microsoft\Cryptography\AutoEnrollment"HKEY_CURRENT_USER\Software\Policies\Microsoft\Cryptography\AutoEnrollmentAEPolicy REG_DWORD 0x7OfflineExpirationPercent REG_DWORD 0xaOfflineExpirationStoreNames REG_SZ MY |
The AEPolicy key should be set to 0x7 in both instances.
After applying the settings, Windows should prompt for certificate Enrollment:



Go to the certificates MMC on the system and ensure the certificate is listed. In active directory users and groups, set smart card required for interactive login:

When the user logs back in, they should now be prompted for the SmartCard PIN to authenticate to the domain.